6 Ways to Defend Yourself Against Viruses and Malware
Leave a reply
Which virus protection is the best?
Well, to protect yourself against malicious software, the six defensive ways detailed below can work better than the best anti-virus software left to act alone.
On a similar note, be careful when downloading files randomly from the Internet. Executable (.exe or .com on Windows) files are the ones that can cause most harm.
In Chrome, copy and paste

In Firefox, go to
While the built-in Windows Firewall provides decent protection, you could try out third-party solutions like ZoneAlarm for better control over what moves in and out of your computer.
I bet if you brush up your knowledge of viruses and run Windows without an anti-virus, you’d be infected fewer times than a noob running an anti-virus on a Windows and not knowing a thing about viruses. Anti-virus software are perfect if you realize that they work best for protecting against viruses that the software already knows about, and not so good at protecting new ones.
Even if there was no danger of infection, backups come in handy in the case of hardware failure, for which you should be prepared for anytime.
Footnotes
//////////////

If you currently have no protection or maintenance software I highly recommend you grab a free scan with PC Matic to see what it can do for you.

You can also create a whitelist so only certain emails get through. You will still have to be careful though, as you do not know what security the sender has installed on their computer. It’s like driving on the road, you need to watch how others are driving to stay safe.
Even if you share files from a cd from a friend, it may have a virus. Protecting your computer from viruses is the most important priority for you and you do not want to risk your computer safety just because you trust your friend.
If you are careful and are serious about learning how to protect your computer from viruses, it is possible to stay safe. My top 10 tips will help you keep your computer running smoothly, and virus free.
Well, to protect yourself against malicious software, the six defensive ways detailed below can work better than the best anti-virus software left to act alone.
1) Be aware of virus symptoms, and attack vectors
This piece of advice might sound something beyond the realm of non-techies. However, non-techies had to learn how to use computers anyway, and learning a little about the basics of viruses won’t hurt. The information contained in this article is a good start.(i) Be wary of suspicious, new process names in the list of running processes
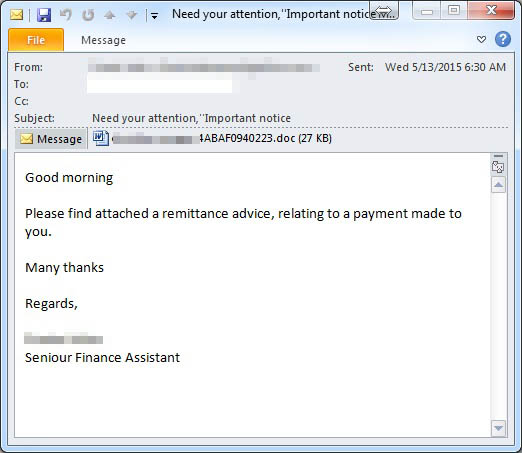
Sometimes these processes have the same names as legitimate ones to disguise themselves (svchost.exe is an example). Sometimes they have similar names, like svvchost.exe and _services.exe (the legitimate ones have the names svchost.exe and services.exe). The username that’s running the process sometimes gives an indication of whether it’s a legitimate system process or not – a virus usually runs under the currently logged-in user’s name. If you’re a power user, you’d want to use Process Explorer, which will allow you to dive in more deeply when inspecting processes, such as figuring out which exact executable on the file system is responsible for the running process.(ii) Emails from your friend may not have been actually sent by them
Be wary of opening email attachments, unless you were expecting them – even seemingly innocuous video files could cause your data to disappear. Take your precautions even when the attachment is expected – the anti-virus scanners embedded with the popular email providers provide a good defense.On a similar note, be careful when downloading files randomly from the Internet. Executable (.exe or .com on Windows) files are the ones that can cause most harm.
(iii) Do not leave the Windows’ auto-run option enabled for portable drives
Auto-run has long been one of the most popular ways in which viruses spread – ensure that you keep it disabled. Never, ever, trust a portable drive that had been previously inserted into a machine that you don’t own, even if it has an anti-virus. Use your anti-virus to scan data that has arrived from external sources. Viruses won’t usually spread through text editors, so you can use these if you’re just inspecting simple files and don’t have an anti-virus at hand.(iv) Watch out for typical virus symptoms, and gear up to protect yourself
These include:- Access disabled to Task Manager, the Registry Editor1, or msconfig2.
- Spikes in CPU or GPU usage – these can be observed either through monitoring tools, such as the Task Manager for the CPU, or GPU-Z for the GPU, or by noticing the hardware fans spinning faster when there is no processor intensive program running.
(v) Safe online banking
Most Linux distributions, including Ubuntu, support booting from a Live CD and are great for providing added protection when banking online, since viruses cannot write to these disks permanently. Live CDs offer no compromise when it comes to your online browsing experience. These Linux distributions can also be installed on bootable USB sticks.2) Choose to manually enable the running of plugins in your browser
Chrome and Firefox have the option of enabling “Click to Play” for plugins (i.e. either Flash or Java) within websites so that they run each time only with your permission which you provide by clicking on the area of the page in which . This will help prevent drive-by attacks from malicious code embedded in such plugins, which are almost always hidden from view, or use some sort of social engineering to trick users into downloading malware.In Chrome, copy and paste
chrome://chrome/settings/content into your address bar, and choose “Click to play” under “Plugins”.
In Firefox, go to
about:plugins, and turn on the plugins.click_to_play option.3) Update your OS, focusing on the security updates
They are called “security” for a reason. This is especially important for the Windows OS. Because of Windows’ popularity, hackers have been known to target security holes in Windows on unpatched machines by studying the fixes Microsoft sends out. This is becoming true even for Mac’s OS X; the recent Java malware is an example –though Apple actually released the update and fix after the Trojan was out in the wild. A Windows example: If you updated before Sasser arrived, you’d be 100% secure.4) Use a firewall
This doesn’t offer much more protection from Internet worms than a NAT, but will be useful if you connect your laptop to a public network. It will also protect yourself from infected machines on your own network. A firewall would protect you from Sasser even if you didn’t install security updates at the time, and would offer partial protection against MSBlast.While the built-in Windows Firewall provides decent protection, you could try out third-party solutions like ZoneAlarm for better control over what moves in and out of your computer.
5) Use an Anti-virus
This is important, but you must know where it stands – it cannot protect you against everything. In fact, most people skip it on the Mac and Linux, though it’s always recommended for Windows. Remember, you are worse off if you use an anti-virus but don’t know how viruses work.I bet if you brush up your knowledge of viruses and run Windows without an anti-virus, you’d be infected fewer times than a noob running an anti-virus on a Windows and not knowing a thing about viruses. Anti-virus software are perfect if you realize that they work best for protecting against viruses that the software already knows about, and not so good at protecting new ones.
6) Backups
Whatever precautions you take, you might still lose the fight. Always ensure that you have important data backed-up, so that you can easily restore it in the case of an infection.Even if there was no danger of infection, backups come in handy in the case of hardware failure, for which you should be prepared for anytime.
Footnotes
- ^The Registry is a database of configuration settings and options related to the Microsoft Windows operating systems. It can be accessed by pressing Ctrl+R, typing regedit.exe and pressing Enter
- ^MSConfig is a Microsoft Windows utility you can use to troubleshoot issues related to processes that are loaded on startup. Viruses often register themselves to start up automatically – you can remove the easier ones using msconfig or by editing the registry.
//////////////
Top 10 Tips to Protect Yourself Against Computer Viruses
10 Tips to Protect Your Computer From Viruses
There are many ways to protect your computer from nasty viruses invading. Protecting your computer is a number one concern for every computer user on earth. I do not know anyone that wants to have their computer crash due to a virus invasion. Here are 10 ways to protect your computer from viruses and keep your files and data safe.1. Learn about viruses
The first thing that I recommend is to research and become knowledgeable about viruses. How can you protect your computer from viruses if you don’t even know what they are. Here are some previous tutorials I have written about viruses. See What is a Virus and how do I know if I have one? and What is the difference between a virus, spyware, Malware, and adware? How can you protect your computer from viruses if you don’t know what it is?2. Arm yourself with the best Anti-virus software to suit your needs.
Not everyone can get away with using free Anti-virus software because it depends what you do on your computer. It depends on factors such as if you download files or not, if you open email attachments, and if you surf suspicious websites. See my reviews for the best Virus Removal Software. Lets face it, if you do not have protection against viruses installed on your computer, you will without a doubt, get a virus within the first hour of surfing the internet. It is that easy. For years I would remove a virus from my dads computer at least once a year, until finally I realized that he needed a paid Anti-virus program. He wasn’t good with computers and if a windows popped up and said he needed to take a scan, he would just do it. He would just presume it was the program I had installed to protect his computer. Now I have installed PC Matic on this computer and there has not been one problem since. This program offers full protection along with full computer maintenance. It never asks him to do anything and just works in the background silently.
If you currently have no protection or maintenance software I highly recommend you grab a free scan with PC Matic to see what it can do for you.
3. Regular Updates
Having a great Anti-virus program installed on your computer to protect your computer from viruses is great, however if you do not regularly update the virus definitions, then the program is useless. New viruses are produced daily and this is why we constantly have to update the viruses definitions and stay ahead of the bad guys. Most programs will update by itself as long as you haven’t turned this option off by accident. This is definitely something you should check.4. Downloading
When surfing the internet avoid websites that contain illegal software downloads, sexual references, free screensavers, cracks or serials, etc. I am sure you get the picture. If you go near these sites you are immediately asking for trouble. Some other websites that you should stay away from include foreign websites where you cannot understand the language on them. This is because you cannot tell what is on the website. This is definitely included in the top 10 internet safety tips.5. Windows Updates
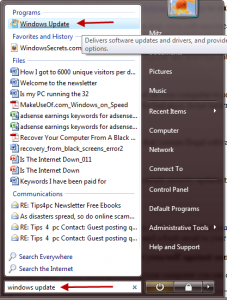
Always update Windows when protecting your computer. These updates contain security updates that will help in your fight against viruses. If you do not perform regular Windows updates you are leaving your computer in a vulnerable state. You can simple check to see if your computer needs updates by going to he start menu and typing in “windows update”. See the screen shot below. You can also view recent Windows update history so you can be in control of the whole situation.
6. Opening Emails
Be careful when opening emails. There are obvious emails that you know you shouldn’t open, however what about the ones you get from people you know? What if your friend has a virus and it is spreading itself through emails? An email cannot be important enough to risk getting a virus. Delete the email and send a fresh email to your friend asking them if they actually did send you the email. It is better to be safe than sorry.You can also create a whitelist so only certain emails get through. You will still have to be careful though, as you do not know what security the sender has installed on their computer. It’s like driving on the road, you need to watch how others are driving to stay safe.
7. Change your settings to protect your computer from viruses
If you are really serious about protecting your computer you can change your email settings and receive text emails only. You can also disable the ability to open email attachments. Virus travel in HTML enabled emails and file attachments. They cannot travel in text email messages. I know this sounds very boring, however, I would rather be boring and protect my computer from viruses.8. Peer to Peer file sharing – ways to protect your computer
Do not use peer to peer (p2p) file sharing programs. These include programs such as Limewire, Bearshare, Gnutella, Morpheus, Torrents, etc. These programs let you download files from other computer users connected to their program network. You have no way of knowing what you are actually downloading until it is on your computer.Even if you share files from a cd from a friend, it may have a virus. Protecting your computer from viruses is the most important priority for you and you do not want to risk your computer safety just because you trust your friend.
9. Do not download files from websites
Again, there is no way of knowing what you are downloading. The file can appear to be named like the file you want, however it could be anything. Most of the time, this is how a virus is unleashed, it usually seems like a harmless, familiar object. If you are looking for a driver for a certain brand of computer then make sure you are getting the download from the genuine website. Many websites on the Internet offer free driver downloads, however, many of them contain viruses. Everything is not what it seems, so be very careful. I would rather use a program to scan my drivers and update them for me. I would not risk downloading a device driver from just any old website. PC Pitstop offers a free driver scan.10. Have Firewall Protection
Make sure you have a firewall enabled on your computer. Windows comes with an inbuilt firewall or you can use a third party firewall program like Zone Alarm. Either way, make sure the firewall is on…To check the Windows Firewall go to the security settings in your control panel.If you are careful and are serious about learning how to protect your computer from viruses, it is possible to stay safe. My top 10 tips will help you keep your computer running smoothly, and virus free.
Notes on tips to protect your computer from viruses:
- These 10 ways to protect your computer from viruses are extremely important tips to follow. If you have had a virus in the past you would know how devastating it is when you lose all of your files and your computer crashes.
- People often try to install more than one anti-virus program to protect their computers from viruses. This is not how to protect your computer from viruses as installing more than one program always causes a problem. You can only install one virus removal program at any one time.